Cyber threat report about Phishing

How does it work?
Phishing incidents start with a malicious actor sending a communication, acting as someone trusted or recognizable. The sender asks the recipient to take any action, often suggesting an urgent need to do so. Victims who fall for the scam may give away sensitive information that costs them.
Why is phishing effective?
Unlike other types of cyber threats, phishing as a practice doesn’t require any technical skills. It is aimed at humans rather than any complex computer system. It doesn’t exploit any vulnerability on electronic devices, instead is solely focused on people who do not double-check their emails/messages.
Types of phishing attacks
The most prominent types of phishing attacks are via emails or messages asking you to act on a hyperlink. Other types are detailed in the figure below:

Having understood the various types of phishing, let’s look at some of the common characteristics.
Common features of phishing
As hackers have become rather smart over time, it’s not always easy to identify a phishing attack. Here are some of the common features of phishing that will help you identify a phishing attempt:
- Lucrative Offers: Eye-catch emails/messages are used to grab the user’s attention
- Sense of Urgency: A dire message is used to compel the user to take action, e.g., account suspended, please verify personal information
- Hyperlinks: The use of malicious web links to trick users onto a replica webpage and obtain their information
- Attachments: Malicious files are sent to the target, usually carrying a payload like ransomware or other viruses
- Unusual Sender: Malicious actors send out these emails/messages
Recent prominent phishing attacks
On July 15, 2020, Twitter suffered a breach that combined elements of social engineering (security) and phishing. A 17-year-old hacker and accomplices set up a fake website resembling Twitter’s internal VPN provider used by remote working employees. Individuals posing as helpdesk staff called multiple Twitter employees, directing them to submit their credentials to the fake VPN website.
Between May 30, 2019, and October 6, 2019, an unauthorized individual gained access to employee email accounts at Golden Entertainment, a Las Vegas, Nevada slot machine operator using an email phishing attack. The attacker had access to one particular email with an attachment containing the Social Security Numbers, Passport numbers, government IDs, and various personal data of multiple company employees and vendors.
In 2018, the company block.one, blockchain, was attacked by a phishing group who sent phishing emails to all customers, aimed at intercepting the user’s cryptocurrency wallet key and a later attack targeted airdrop token.
What can businesses do?
As per APWG, Q1 of this year witnessed one million plus phishing attacks, including a 7 per cent increase in credential theft phishing. The financial sector suffered the highest percentage of these attacks (approx. 23 per cent).
Let’s look at some useful practices that can protect businesses from such malicious attacks:

What to do in case of suffering a phishing attack?
There are 2 things that might have happened. Either you downloaded a malicious file or gave away your credentials/personal information on a proxy website. Remember, the most important thing is to stay calm and not panic.
If you have downloaded a malicious file:

And, in case you have given away your credentials:
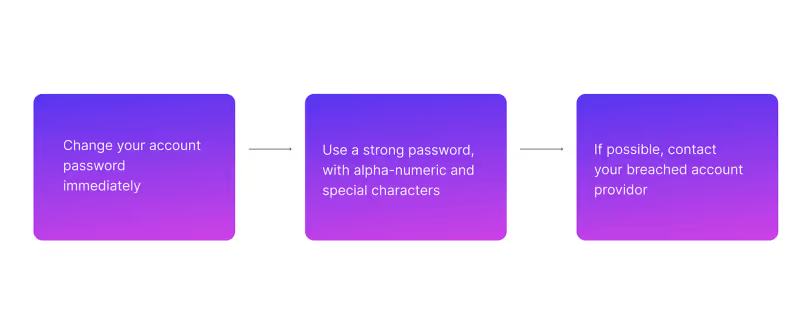
Remember: accord to your business-security policy and inform your IT department if need be.
Conclusion
Phishing attacks have been increasing every year. Understanding the various types of phishing along with some common features will help businesses quickly identify such malicious emails/messages and protect their information better. In case, an employee does suffer an attack, the article provides a few necessary steps to recover from any damage.
Check out Phishing protection offerings from Ofofo.









